On 16 June 2025, AWS announced a new enhancement to AWS Network Firewall: native integration with AWS Transit Gateway. Initially, this feature was supported in a few regions, but as of 8 July, it became available across all AWS regions.
What does the native integration do?
Previously, connecting AWS Network Firewall to AWS Transit Gateway required creating and managing a dedicated VPC with subnets and route tables. With native integration, you can now directly attach your Network Firewall to your Transit Gateway, eliminating the need for additional VPCs or complex routing configurations.
This feature enables East-West inspection, meaning it can inspect traffic between VPCs or between on-premises environments (S2S VPN or Direct Connect) and VPC traffic.
How does the architecture work?
The diagram below illustrates a typical deployment:
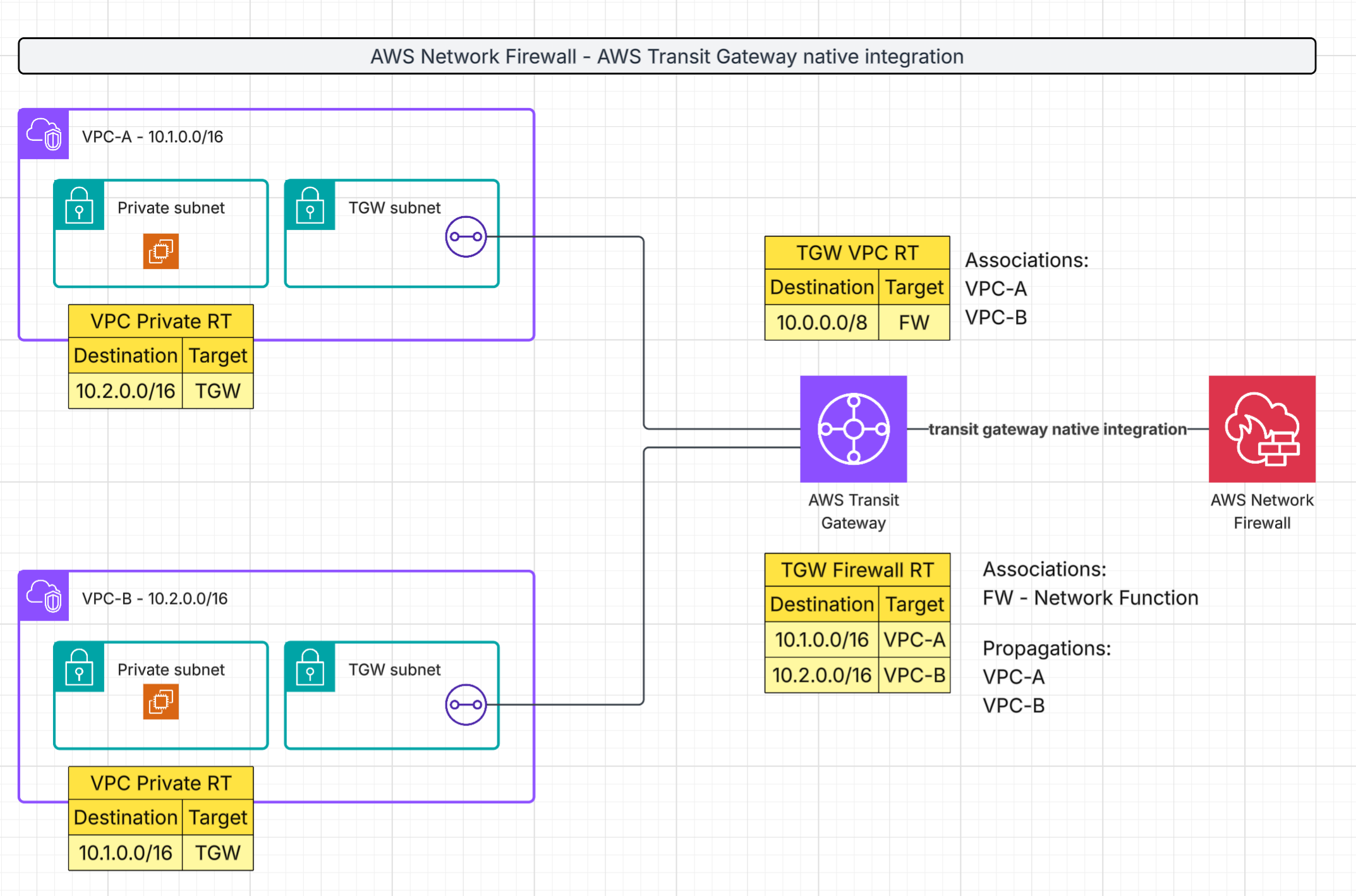
Components:
VPC-A (10.1.0.0/16) and VPC-B (10.2.0.0/16): Application VPCs with private subnets and dedicated subnets for Transit Gateway attachments.
AWS Transit Gateway (TGW): Acts as the central hub for interconnecting multiple VPCs and on-premises network.
AWS Network Firewall: Connected natively to the Transit Gateway, providing centralized inspection and policy enforcement.
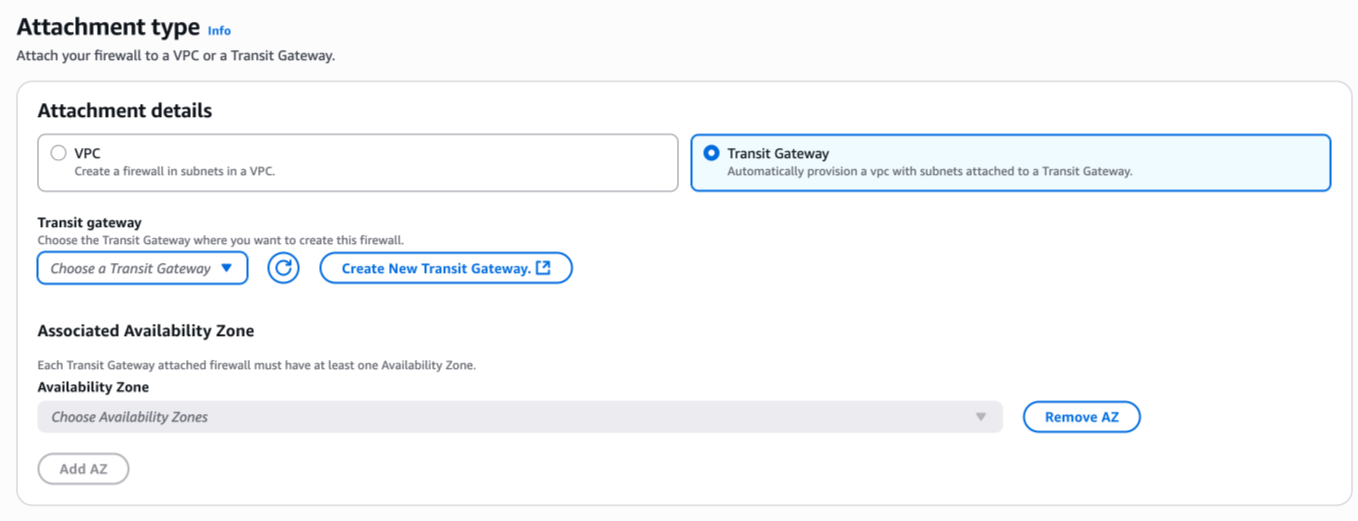
During creation, at the second step, you need to choose the attachment type for the Transit Gateway.
VPC Route Tables: VPCs direct inter-VPC traffic through the Transit Gateway. Note that, with previous deployment types, traffic was directed to the VPC endpoint (Firewall), not the TGW.
Transit Gateway Route Tables:
- TGW VPC Route Table: Both application VPCs are associated with this route table, and a static route to 10.0.0.0/8 is created, pointed to the network function (AWS Network Firewall).
- TGW Firewall Route Table: The Network Firewall is associated with this route table, and the application VPCs CIDR blocks are propagated here.